
User behavior MFA using the BehavioSec Authenticator
On this page
The BehavioSec Cloud service provides risk metrics that can be used to enrich authentication. The users typing pattern when entering username and password is captured during the authentication process. The data is used to build a user profile during an initial training phase. When the user is trained, the typing pattern of subsequent authentications is matched against the profile to determine if the user is the same. BehavioSec uses the data to calculate a risk score. Actions can be taken if the risk is high, require MFA for example, in order to further trust that the user is who they claim to be.
This Authenticator captures the typing pattern in the frontend and passes that data together with a journeyId to BehavioSec Cloud. The backend part of the authenticator can then lookup the risk metrics and add these to the authentication context attributes.
Authentication actions can be added to the authenticator to complete the flow and force MFA if the risk is high or if the user is not yet trained.
The overall result is a username-password authenticator that seamlessly captures behavioral data that calculates a risk score used to trigger MFA. Note that MFA is only triggered in the event that the risk is high and would therefore significantly reduce the number of times a user is required to perform MFA.
Prerequisites
- An installation of Curity Identity Server with the basic setup completed. You can achieve this by following the Getting Started Guides.
- A BehavioSec Cloud Account with a generated API Key/Secret.
Installing the Plugin
Clone the BehavioSec Authenticator GitHub repository and follow the instructions in the readme in the repo.
Versions prior to 6.7 of the Curity Identity Server
The file csp.vm needs to be updated in order for the BehavioSec Cloud API to be called. The needed variable is already set in get.vm, but csp.vm needs to be updated to read that variable.
Locate csp.vm in idsvr/usr/share/templates/core/fragments/ and make the changes outlined below.
Add the following if/else statement after the ones that are already defined.
#if(${_cspConnectSrc})#set ($connectSrc = ${_cspConnectSrc})#else#set ($connectSrc = "connect-src 'self';")#end
Then replace this row:
<meta http-equiv="Content-Security-Policy" content="connect-src 'self'; font-src 'self'; $childSrc">
with this:
<meta http-equiv="Content-Security-Policy" content="$!connectSrc font-src 'self';">
Configuration
| Configuration | Note |
|---|---|
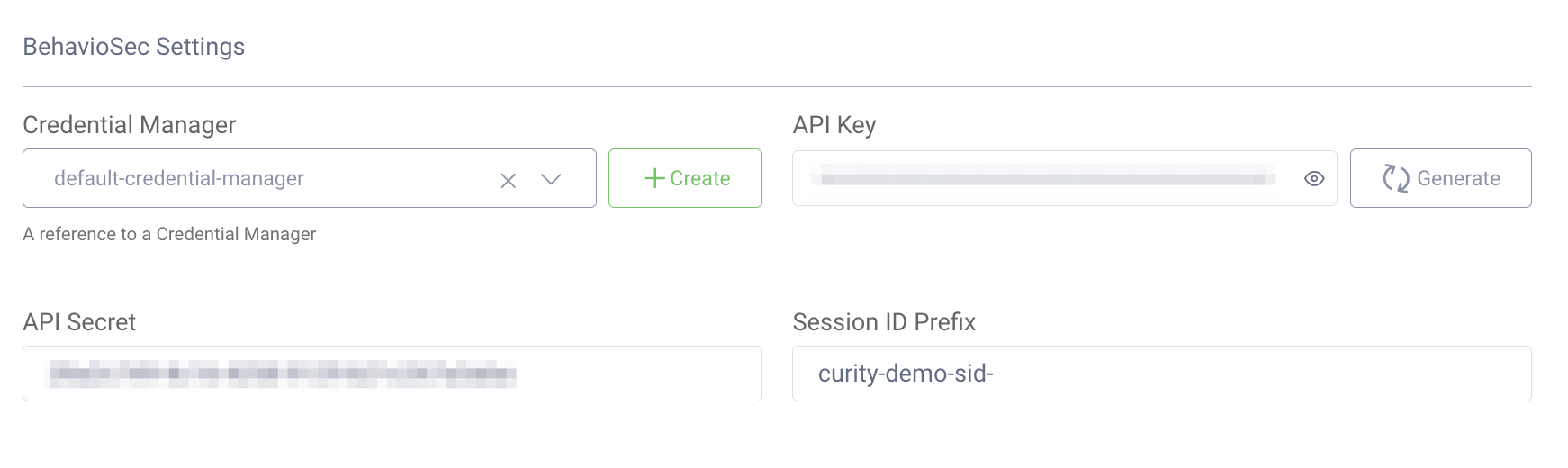
| Credential Manager | A Credential Manager used for user credential verification. |
| API Key | The BehavioSec Cloud API Key. This can be obtained from BehavioSec Cloud. |
| API Secret | The BehavioSec Cloud API Secret. This can be obtained from BehavioSec Cloud. |
| Session ID Prefix | The prefix added to the BehavioSec sessions. Defaults to curity-demo-sid-. |
Screenshot from the Curity Identity Server Admin UI:
Authentication Actions
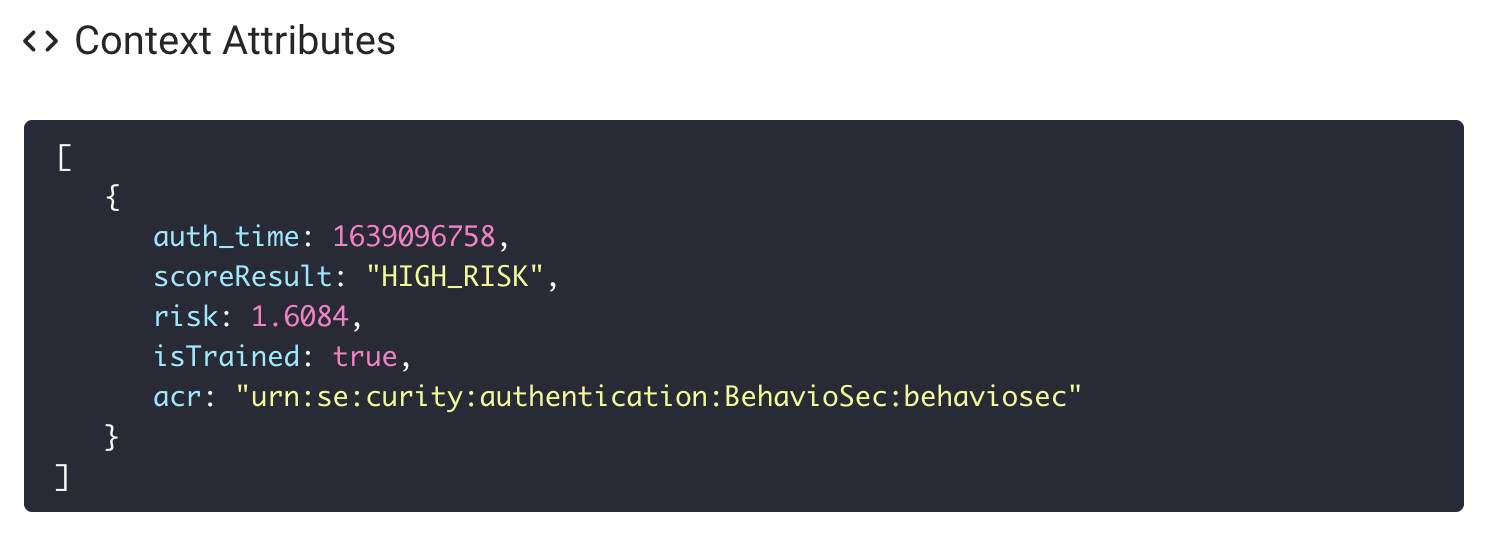
The BehavioSec Authenticator performs credential verification. After a successful authentication the timing data (key stroke information) is sent to BehavioSec Cloud. The return data contains 3 values that the authenticator will add to the context attributes:
| Attribute | Data Type | Example Value |
|---|---|---|
isTrained | Boolean | true, false |
scoreResult | Enum | HIGH_RISK, LOW_RISK |
risk | Decimal | 0.002 |
The Debug Action can be used to show the values:
Switch Action
In this example, a switch action is added to the authenticator to act on the isTrained and scoreResult values. The goal is to trigger MFA if the user is not trained or if the risk score is high. The Switch action looks for these context attributes and if there is a match to the statement configured a script will be invoked.
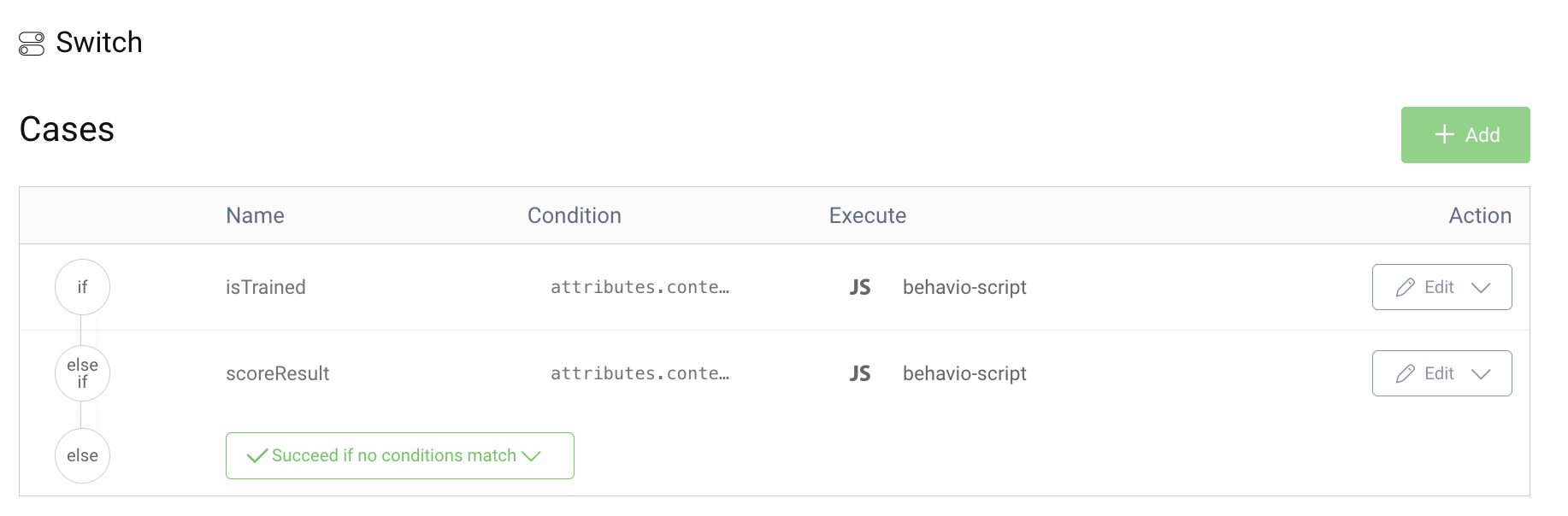
The condition for isTrained is defined as attributes.context.isTrained === false
The condition for scoreResult is defined as attributes.context.scoreResult != "LOW_RISK"
Script Action
The script invoked by the Switch Action sets the attribute requireSecondFactor = true.
function result(transformationContext) {var attributes = transformationContext.attributeMap;attributes.requireSecondFactor = true;return attributes;}
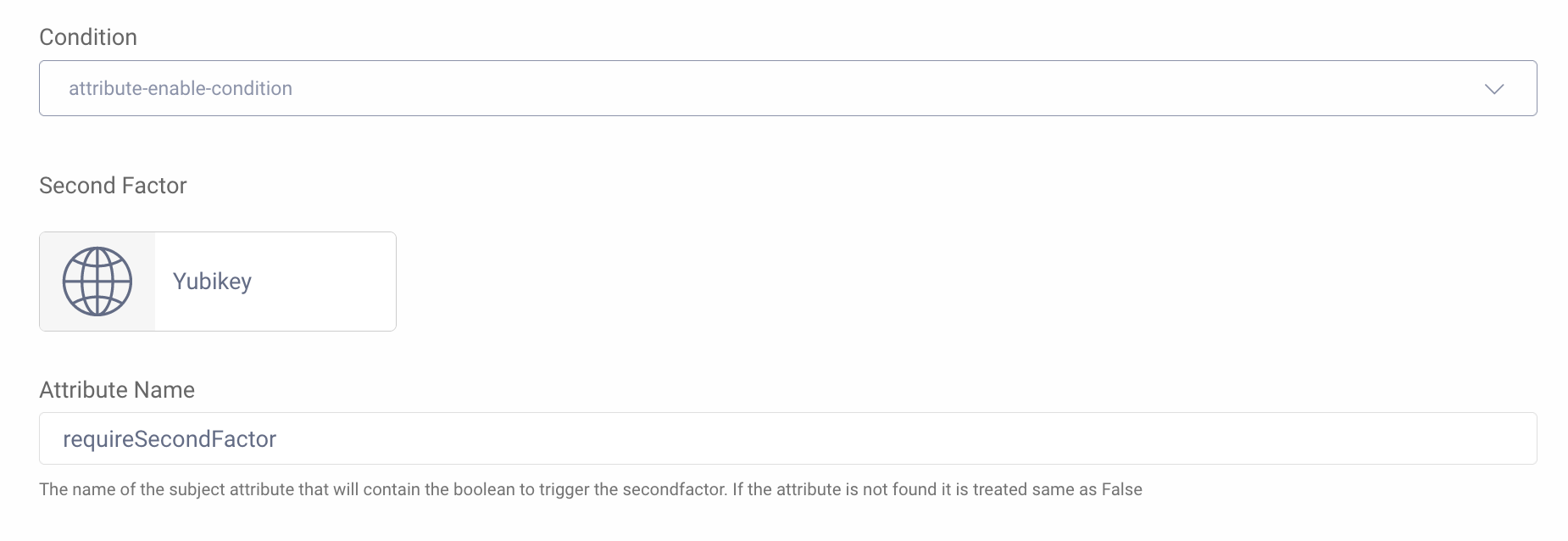
MFA Action
The MFA Action is triggered only when requireSecondFactor == true as set by the script. Any Authenticator can be configured as the second factor in the MFA Action. This example uses a WebAuthn Authenticator configured for use with a YubiKey.
Conclusion
BehavioSec Cloud provides a unique methodology of determining the key press timing of a user entering their username and password. The timing information is matched against a profile established for each user and thus a risk score can be calculated for the authentication. The risk score can be used to minimize the invocation of MFA for the user and with allow for a more seamless authentication on a regular basis. MFA is only triggered when there is a higher risk calculated and stronger mechanism for authenticating the user is needed.
Refer to the BehavioSec Cloud Docs for more details on BehavioSec Cloud.
Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.
Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free Trial


