
DevOps Dashboard Overview
On this page
The Curity Identity Server includes a DevOps Dashboard, as a simplified Admin UI that enables employees to manage identity resources. This enables organizations to scale their administration of the identity and access management (IAM) system to multiple teams, to avoid bottlenecks on a central team. Teams can be separated into groups with different administration rights. The DevOps dashboard webinar provides a video intro.
Administer Customer Users
One of the main features of the dashboard is to administer user accounts from a data source. This provides a fast way to precreate application users when getting started with the Curity Identity Server, or in scenarios where end users cannot register themselves:
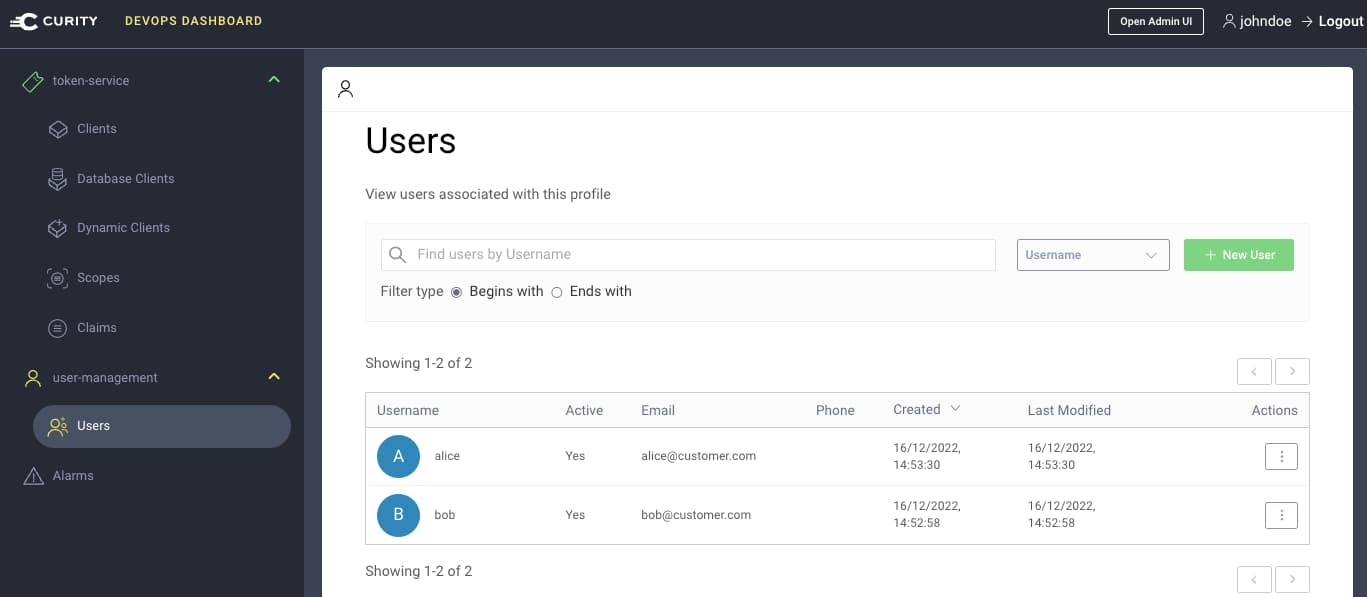
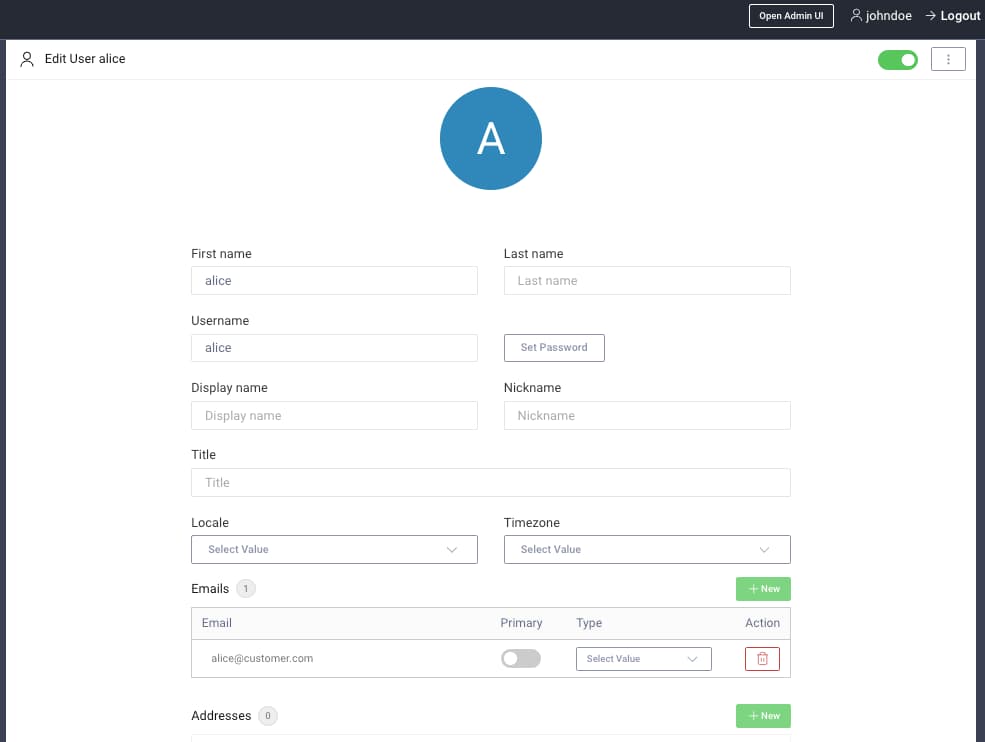
In the following example, a DevOps employee called johndoe is administering a customer user called alice:
Grant Team Privileges
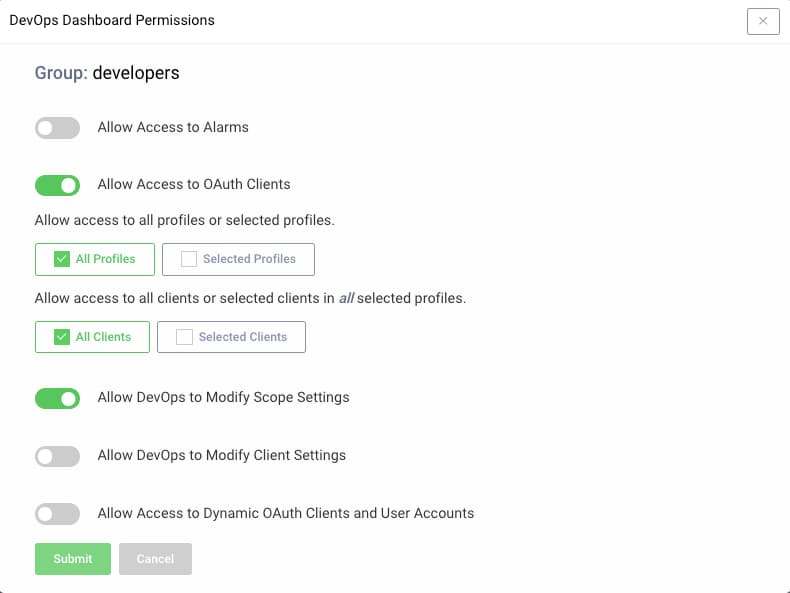
When granting access to employees, categorize them into groups based on the levels of access you want to grant. In the following screenshot, members of the developers group are denied access to customer user accounts, but are allowed to work with settings for their OAuth clients and APIs:
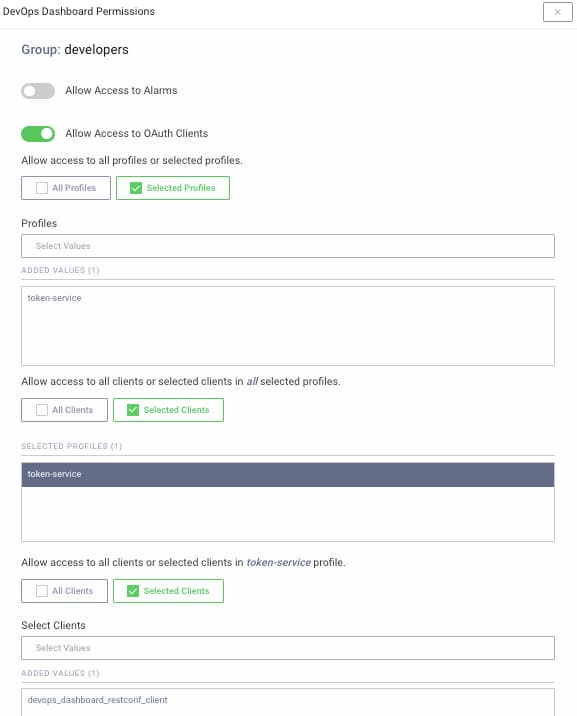
Permissions can be granted in a manner that scales up to departmental boundaries, or down to individual clients. This enables larger organizations to distribute access based on levels of experience or trust:
If an employee has insufficient permissions, and the data shown is sensitive, such as for customer user accounts, then a permission denied message is displayed. In other cases, the user may be able to attempt an edit, such as creating a new scope, and will receive a forbidden error upon trying to save changes:
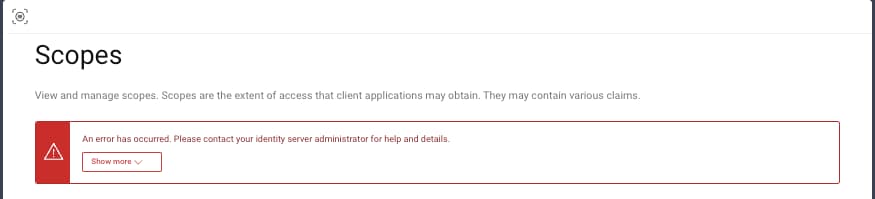
Manage Application OAuth Settings
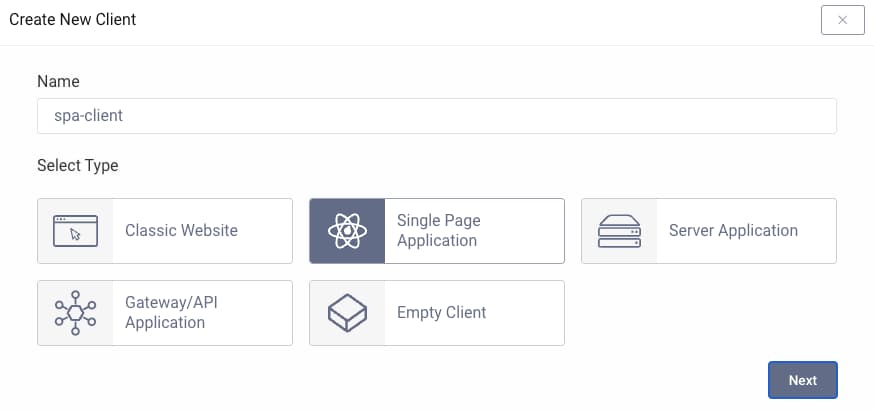
With the above permissions, a member of the developers group would be able to perform operations such as reading or editing client settings for frontends, or scopes and claims received by APIs. The dashboard also provides a simplified wizard for creating new OAuth clients, in a developer focused manner:
Share Operational Troubleshooting
In the event of technical problems, you can enable multiple teams to help diagnose the cause. The alarms feature highlights any connectivity problems the Curity Identity Server is experiencing. In some cases, the teams who work on the applications impacted may be best able to advise on resolution actions.
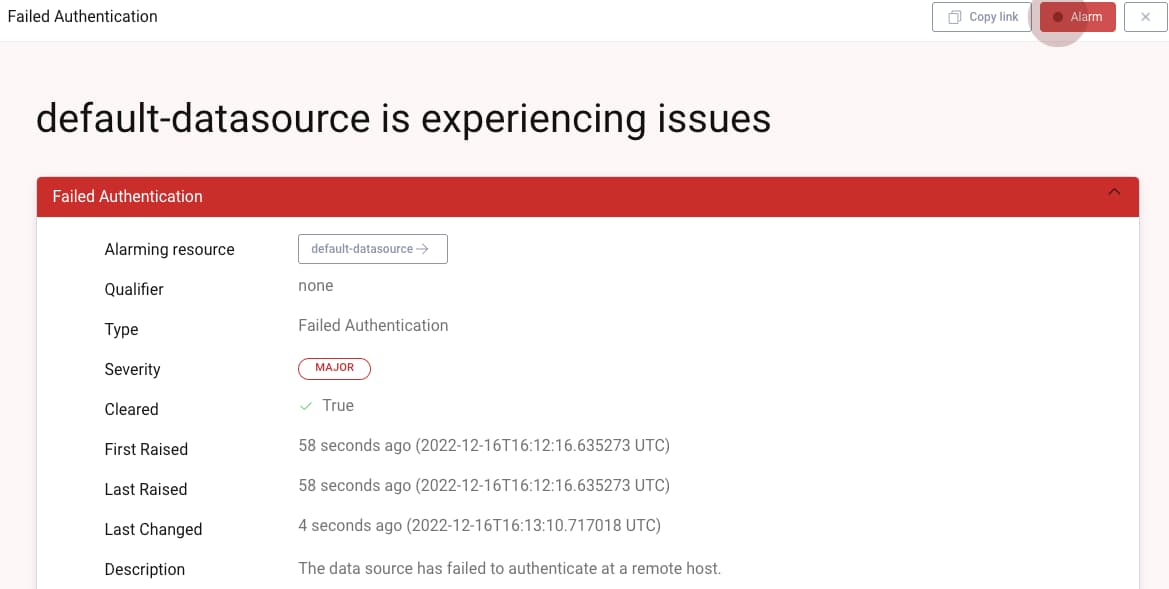
Conclusion
The DevOps dashboard provides additional administration options for the Curity Identity Server. Use it to administer your end users, or to distribute your identity management across teams. To get started with the dashboard, see the Running the DevOps Dashboard tutorial.

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free Trial


