
Authenticate Using Microsoft Entra ID
On this page
OIDC with Microsoft Entra ID
This tutorial shows how to authenticate to the Curity Identity Server from Microsoft Entra ID. This is achieved by using the Open ID Connect authenticator in the Curity Identity Server and setting up the Curity Identity Server as an application in Microsoft Entra ID. If you want to authenticate the other way around, using the Curity Identity Server to login to Microsoft Entra ID, follow this tutorial Integrating with Microsoft Entra ID.
Start by creating an OIDC authenticator in the Curity Identity Server. Enter a name for the authenticator and click Create. Copy the name of the authenticator from the top. We will fill in the rest after we are done in Microsoft Entra ID.
Register an application in Microsoft Entra ID
In Microsoft Entra ID select App registrations and then New registration.
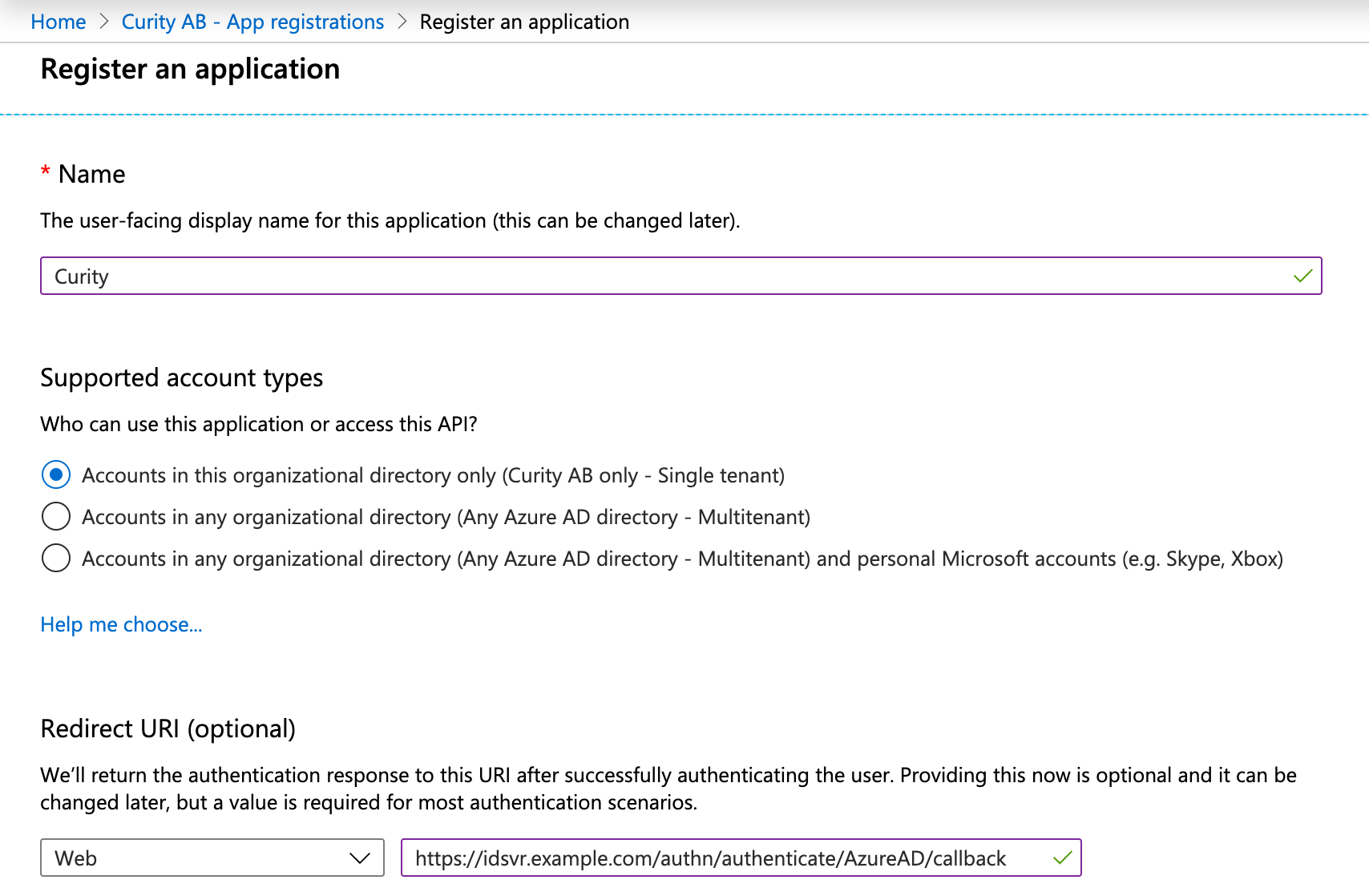 Set name and who should be able to use this.
Set name and who should be able to use this.
In Redirect URI, select Web and then enter the redirect URL of your Microsoft Entra ID authenticator. It is <BASE URL>/<AUTHENTICATION ENDPOINT>/<AUTHENTICATOR NAME>/callback.
The result should look something like this if your authenticator is EntraID, https://idsvr.example.com/authn/authenticate/EntraID/callback
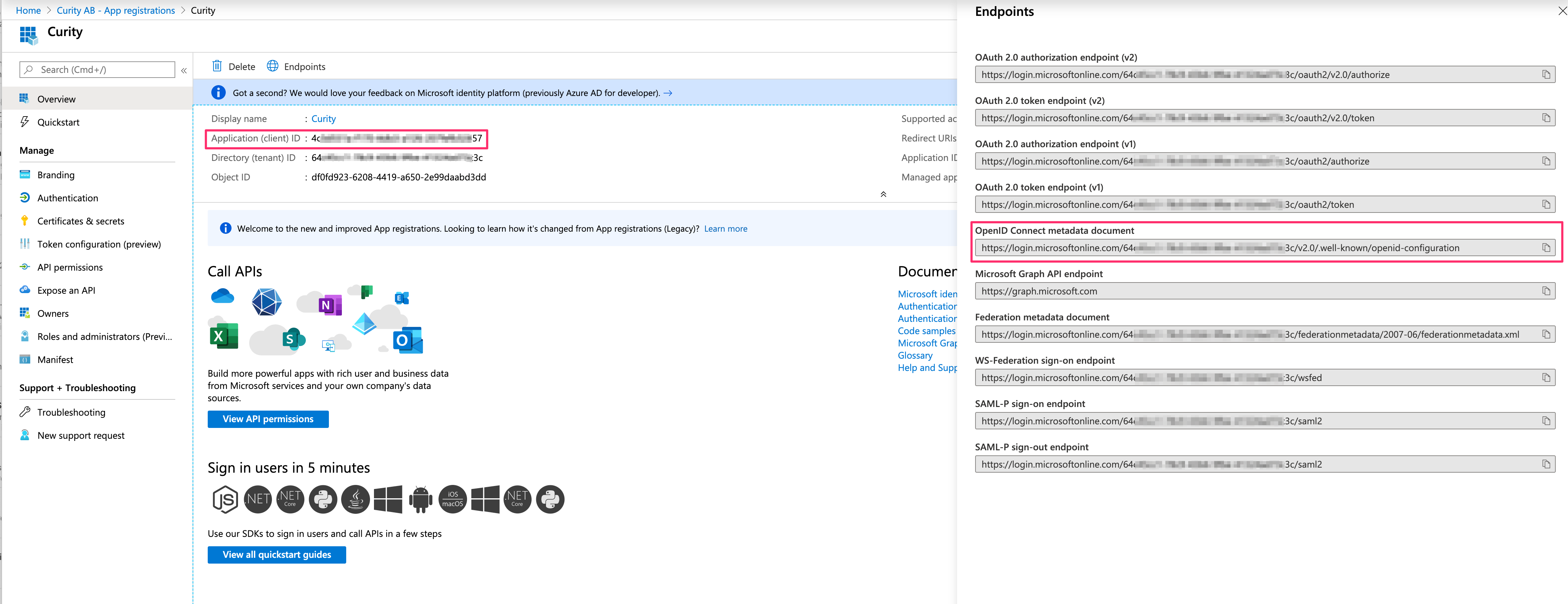 When the application is registered, navigate to the Overview. Click on Endpoints and make a note of
When the application is registered, navigate to the Overview. Click on Endpoints and make a note of Application (client) ID and OpenID Connect metadata document, you will need them later.
Next up is to create a secret. Navigate to Certificates & secrets.
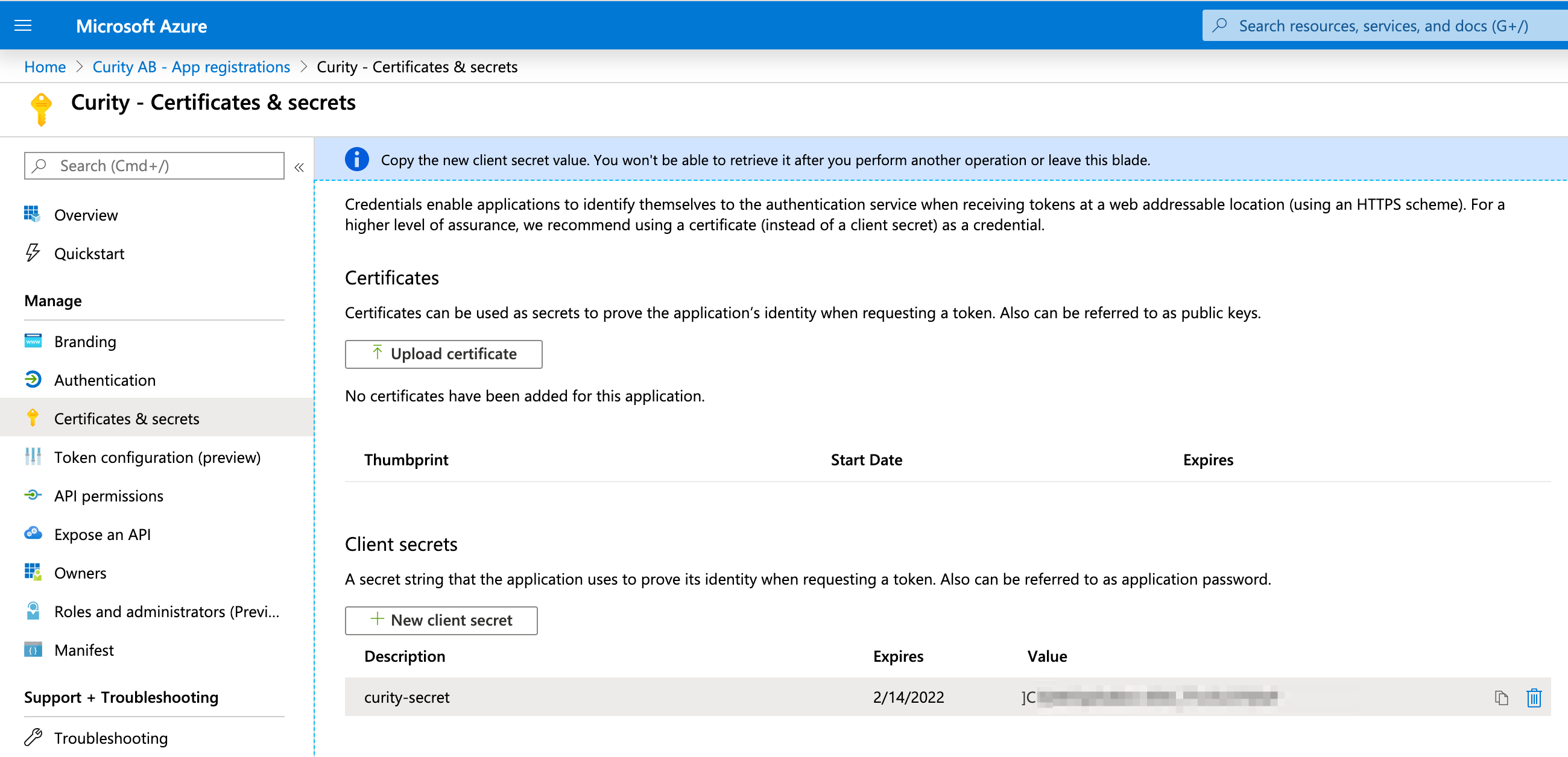 Click on New client secret, give it a name and a validity time.
After pressing Add, make a note of the generated secret.
Click on New client secret, give it a name and a validity time.
After pressing Add, make a note of the generated secret.
Attention
After leaving this page you cannot see the secret again.
Configuring the OIDC connector
Getting back to the new OIDC authenticator we now have all the information we need to finalize it.
- First of all, we have to set the
Configuration URL. This is theOpen ID metadataURL. - Then we enter the
Client ID, which we noted earlier. Scopemust includeopenid.- Set
Client authentication methodtoclient-secret. TheClient Secretis the secret you previously generated. - Don´t forget to commit your changes when done.
Summary
Using your new OIDC authenticator you should be able to login with your Microsoft Entra ID account to Curity Identity Server. Microsoft Entra ID supports other scopes and can return other claims which can be used by the Curity Identity Server but it is not part of this article. More information can be found in Microsoft Docs.

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free Trial


