On this page
This article describes how to enable the Phantom Token Pattern by using a custom policy developed for the Mulesoft Flex API Gateway. The details of the OAuth Introspection and Phantom Tokens is a useful read before diving fully into how to set up this integration.
Prerequisites
- An installation of the Curity Identity Server.
- Basic understanding of Mulesoft Flex and the Mulesoft Anypoint Platform.
If you do not have an installation of the Curity Identity Server, follow this tutorial installation of the Curity Identity Server and configure the installation by running Curity Basic Setup Wizard as outlined in this tutorial Curity Basic Setup Wizard.
Configure the Curity Identity Server
The custom Mulesoft Flex policy can handle both the application/jwt approach as well as the approach where the phantom token is returned in the phantom_token attribute in the introspection response. Both approaches are outlined and explained in the OAuth Introspection and Phantom Tokens article.
The application/jwt approach is enabled and supported out-of-the-box in the Curity Identity Server. No extra configuration is needed if that approach is used.
Compile, Deploy and Configure the Mulesoft Flex Phantom Token Policy
The code for the Mulesoft Flex Phantom Token Policy is available in the GitHub repository together with instructions for how to compile, deploy and configure.
Create & Configure the Policy
- Log in to the Mulesoft Anypoint Platform
- From the menu, navigate to API Manager
- Select an API to apply the Phantom Token pattern to
- Choose Policies from the menu on the left
- Click
+ Add policy
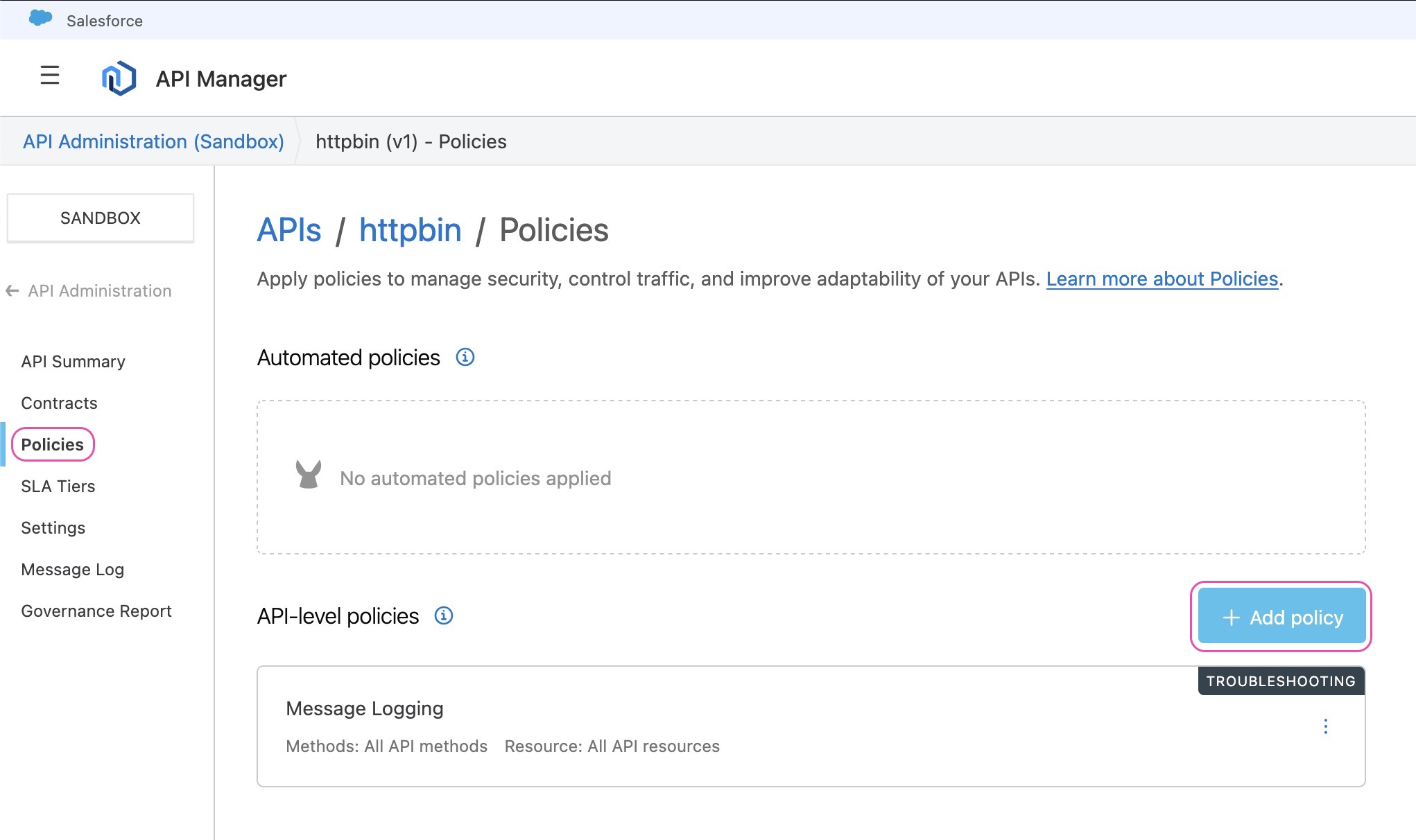
- With the custom policy uploaded using either
make publishormake releaseit should be available to select from the Security category. Select it and click Next. Note that this might be suffixed withDEVif the policy is Published but not Released.
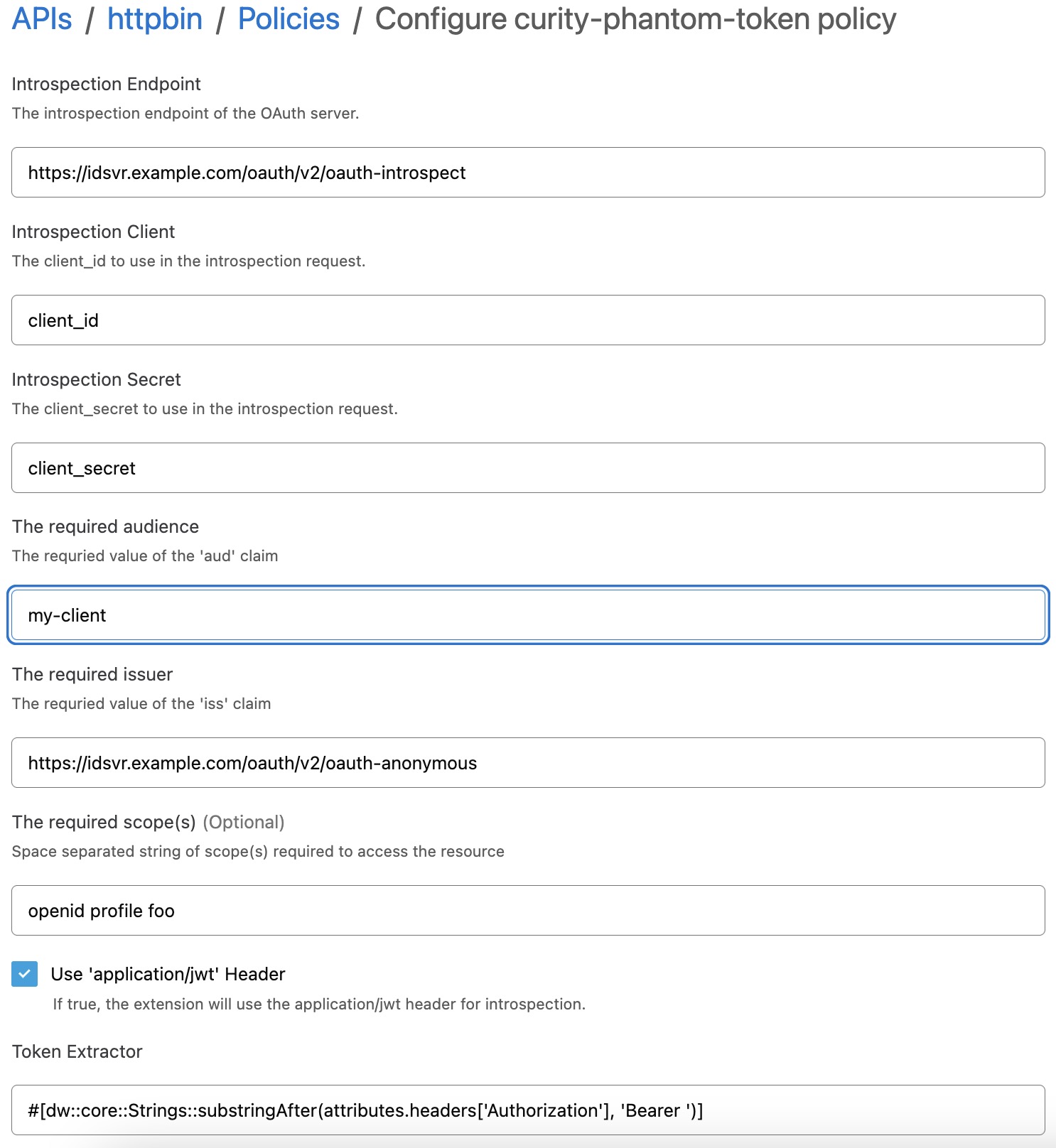
- Configure the policy with the parameters needed for your environment and click Apply. The configuration parameters are detailed in the policy code README.
Test the Integration
To test the integration, obtain an opaque access token. This can be done using OAuth Tools.
Next make a request to the API exposed by the Mulesoft Flex API Gateway. This could also be done in OAuth Tools by using the External API Flow. Here's an example using curl:
curl -Ss -X GET http://my-api.example.com/httpbin/get \-H 'Authorization: Bearer _0XBPWQQ_bf0caf4f-5378-43e1-9c08-09201cc75d4b'
Example response from Httpbin (Authorization header abbreviated for readability):
{"args": {},"headers": {"Accept": "application/json, text/plain, */*","Accept-Encoding": "gzip, compress, deflate, br","Authorization": "eyJraWQi..iKiwjQ","Host": "httpbin.org","User-Agent": "axios/1.7.7","X-Amzn-Trace-Id": "Root=1-67d46806-3f4ba5a14641ba052d546f35","X-Envoy-Expected-Rq-Timeout-Ms": "15000","X-Envoy-External-Address": "99.167.203.24","X-Envoy-Original-Path": "/httpbin/"},"origin": "99.167.203.24, 3.89.74.49","url": "https://httpbin.org/"}
Httpbin is a test API that will echo back what is sent to it. In this case that the request to Mulesoft included an opaque token in the Authorization header but the actual API (Httpbin in this case) received a JWT in the Authorization header.
Resources
Useful resources that cover the topics of this article.
- An article on OAuth Introspection and Phantom Tokens
- Mulesoft Anypoint Platform Gateways
- Flex Gateway Policy Development Kit (PDK) Overview

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free TrialWas this helpful?
