
iOS Client Setup for the Hypermedia Authentication API
On this page
What Is the Hypermedia Authentication API?
The Hypermedia Authentication API is a feature of the Curity Identity Server. It enables clients to leverage OAuth and OpenID Connect and the Curity Identity Server's powerful authentication engine straight from client applications — without the need of a browser. If you want to learn more about the Hypermedia Authentication API, check out the overview article.
It's All About Security
The browser plays a vital role in OAuth and OIDC flows — it makes them more secure. Browser redirects ensure that the Authorization Server delivers data to the proper client, and not to an impersonator. Thus, removing the browser from OAuth and OIDC flows may at first seem a bit reckless. As we now use an API to fulfill a vulnerable authentication and authorization flow, we require another method to make sure that the client calling the API is indeed allowed to do so.
Two security features of the Curity Identity Server ensure that the Authentication API process is just as secure as browser flows:
- client attestation
- proof of possession tokens
Client Attestation
Client attestation is done by verifying the running application's package ID and the signing credentials. This is processed by the Android Operation System or iOS and bound to a cryptographic key pair. After a positive attestation, the client (the mobile app) is issued a Client Attestation Token (CAT) in the form of a JWT. The concrete implementation of the attestation is out of the scope of this article, but what is important to note, is that client attestation asserts a few things about the calling client application:
- The app was correctly signed with the credentials configured in the Curity Identity Server for the associated OAuth client. This means that the app has not been tampered with. For example, it hasn't been decompiled, had its code changed, and recompiled into a malicious client. When using these features, decompilation cannot provide any information that could help create an impersonated client.
- The app runs in a safe environment, that is, on a system that has not been rooted. Otherwise, it wouldn't be possible to securely perform the verification described above.
Demonstrating Proof of Possession
Proof-of-Possession tokens are another way to use access tokens. The most common way used in APIs is using Bearer tokens. Bearer tokens work a bit like cash — any client who possesses a Bearer access token can successfully call an API. Proof-of-Possession tokens behave more like credit cards — only legitimate owners of these tokens can use them to access the API. This further increases the security of the communication. Even if the access token is stolen, another party can't use it.
The Hypermedia Authentication API uses a standard for Demonstrating Proof of Possession. By adopting this standard, access tokens used to access the Authentication API are bound to a private key that only the legitimate client possesses.
Roles of HAAPI SDKs
To facilitate the usage of these crucial security components, Curity has released SDKs to help you leverage the Hypermedia API:
| Library | Responsibilities |
|---|---|
| UI SDK | A HAAPI client that receives API responses and renders views. It manages valid and invalid input, redirects, navigation, polling, and many other behaviors. The default look and feel can be customized. All of this means you can implement a HAAPI flow with only a couple of lines of code. |
| Model SDK | The model SDK introduces classes representing possible responses from the authentication API. The model SDK uses the driver SDK to handle communication, then processes responses into models. These represent the instructions the API is issuing to the mobile client. |
| Driver SDK | Obtaining CATs and using DPoP to secure requests to the API is a security-sensitive process. Obtaining a CAT requires a few different steps, and the DPoP standard requires the client to generate correct headers for every request. The driver SDK is responsible for handling these low-level security concerns. |
It is only necessary to use the UI SDK, which provides a high level interface, to get up and running with a HAAPI secured mobile app. The SDK performs generic rendering of API responses, using Hypermedia API responses. An alternative approach, which currently gives you greater control over custom rendering, is to instead use the model SDK directly.
Prerequisite Setup
To call the API from an iOS app, you must register an iOS attestation policy. To add one, follow the instructions below:
- Open the Facilities menu in the top right corner of the admin UI and navigate to Client Attestations at the bottom.
- Click on the + button next to iOS Policies.
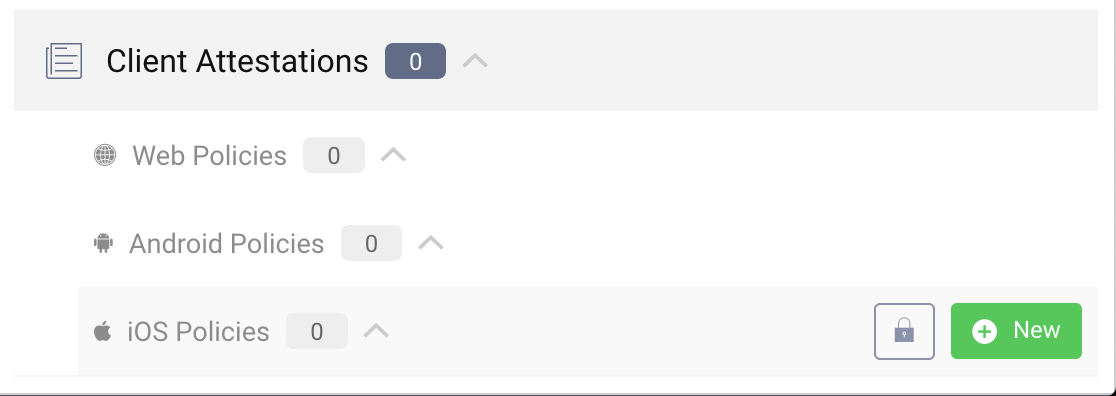
- Enter a suitable name for the policy and click Create.
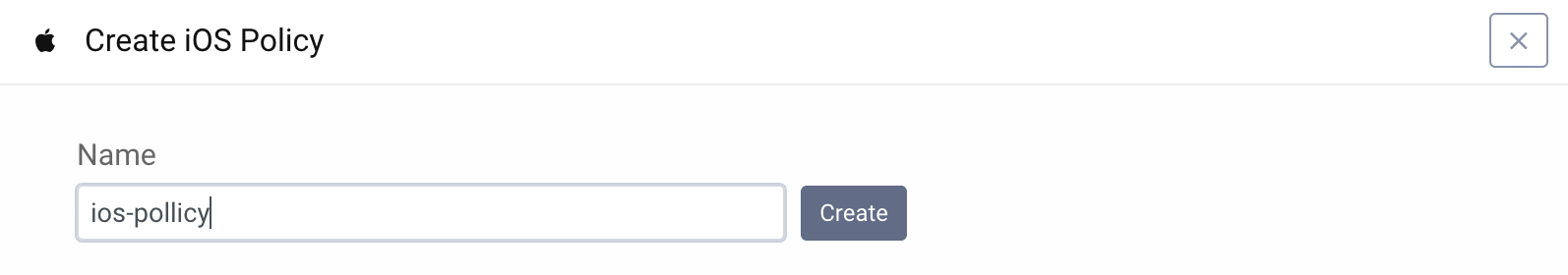
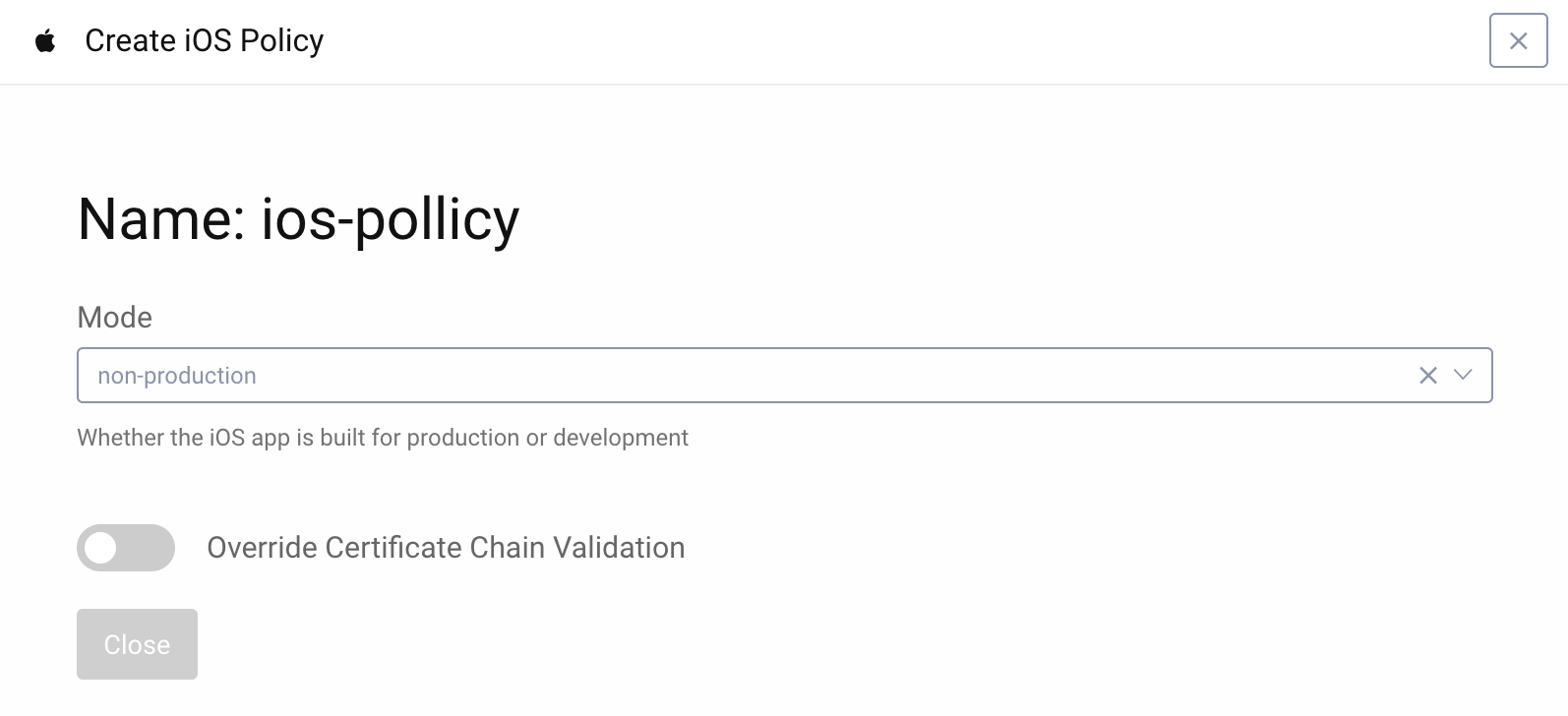
- Choose the appropriate mode.
productionmode tells the Curity Identity Server to validate the app against its release signing settings. Choosingnon-productionwill validate the app against the debug signing settings. In some rare cases, it might also be necessary to overwrite Apple's Certificate Chain, but normally you shouldn't need to use this setting. Close the dialog once you choose all the settings.
-
You will also need a client with the HAAPI capability which uses the iOS attestation policy.
- Go to Profiles → Token Service → Clients, and edit the client of your choice.
- In the Capabilities section, make sure your client has at least these two enabled:
Hypermedia Authentication APIandCode Flow. Use any URL for the redirect URL (e.g.https://localhost) and chooseno-authenticationas the Client authentication method. - Scroll down to the Client Application Settings tab and open the Advanced section. Enable the Attestation, and select
iosas attestation type. Enter your App ID following the instructions available next to the input field and choose the Attestation Policy that you've previously created. - If you want to test or develop the app using a simulated device turn on the Disable Attestation Validation option. When this is on, the client and server will still perform the Attestation, but the server will not validate the attestation. Attestation functionality does not work on simulated iOS devices, so you have to enable this option when using a simulator. Remember not to use this setting for production clients!
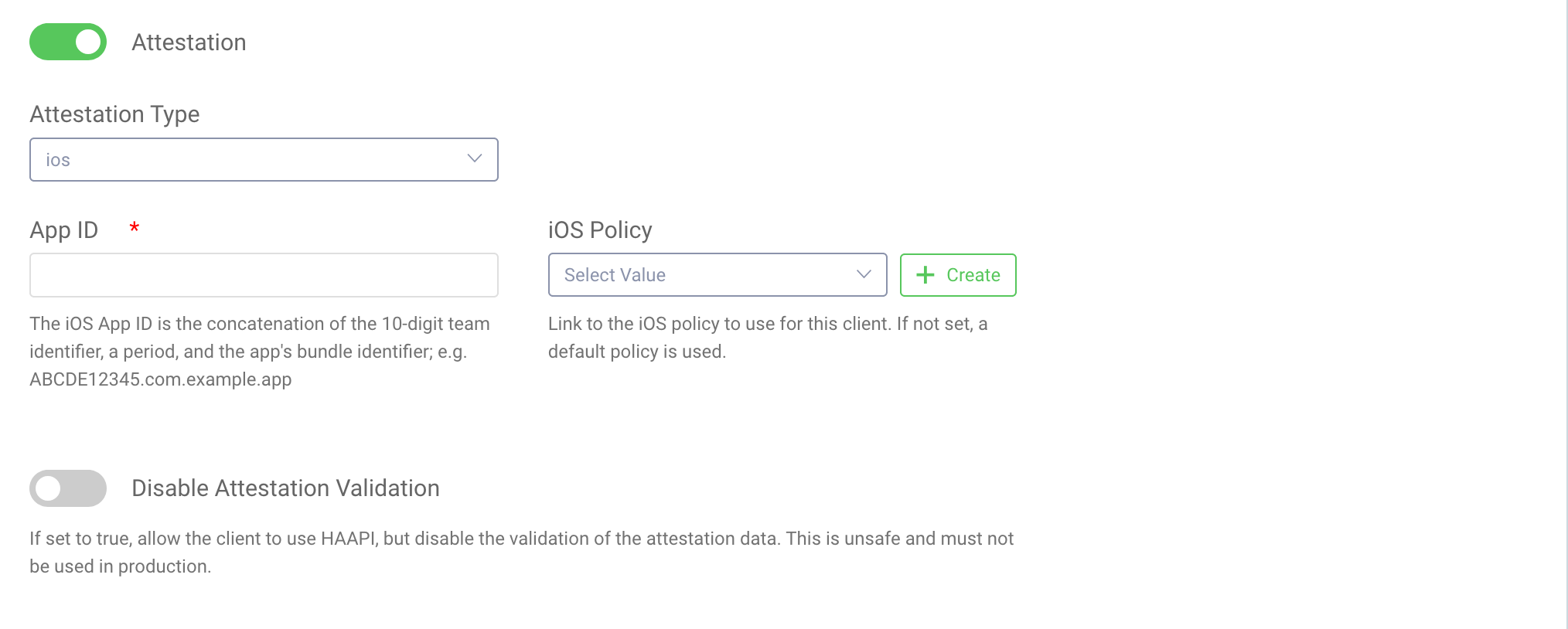
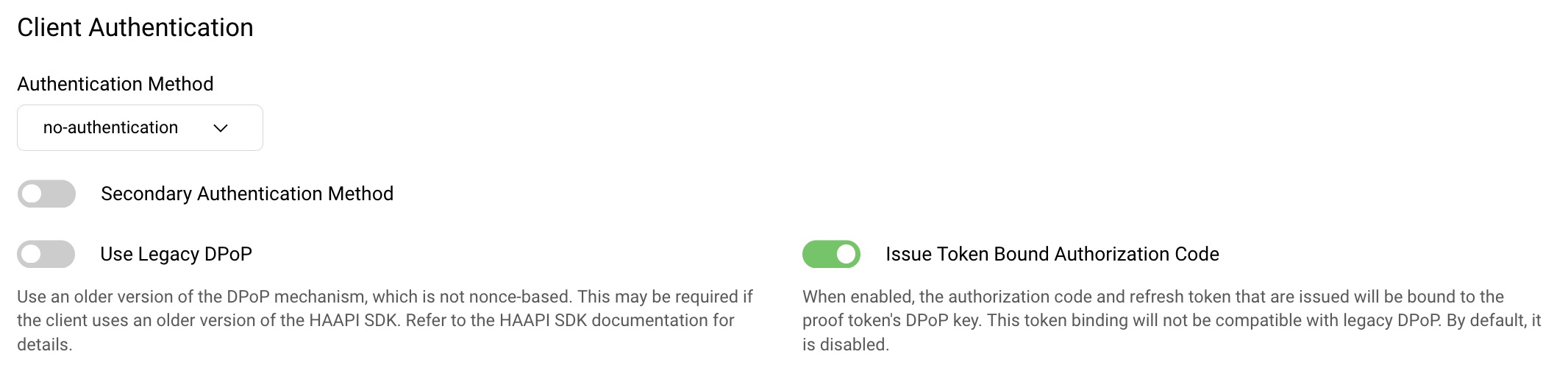
Configure Client Settings
Leave the Use Legacy DPoP setting deselected to prevent potential clock synchronization issues during HAAPI flows. The Issue Token Bound Authorization Code setting should also be enabled, if you are using version 3.2 or higher of the iOS HAAPI UI SDK and version 8.7 or higher of the Curity Identity Server. The token bound setting provides additional security for token requests. You can read more about it in the HAAPI Mobile Security Lifecycle tutorial.
Integrate HAAPI into a Mobile App
Now that the security setup is done, you can quickly integrate mobile security into your app, by following the iOS integration tutorial. Also checkout the iOS Swift HAAPI Code Example, which provides an automated setup and demonstrates some customization techniques.
Conclusion
To use the hypermedia authentication API in a mobile app you first must do some prerequisite setup and integrate the Curity SDKs. You can then quickly integrate a hardened OpenID Connect flow into your mobile app.
For further details on the API, have a look at the Authentication API documentation. If you need help setting up the API or SDK, or have any other questions or comments, please do not hesitate to contact us.

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free TrialWas this helpful?



