
Setting up OpenID Connect Authentication in the Kong Developer Portal
On this page
The Kong Developer Portal is a part of Kong Enterprise Gateway. The portal enables developers to access and manage configured services and documentation to provide a streamlined onboarding process. The Kong Dev Portal supports various options for user authentication and access control. This article outlines how to configure the Kong OpenID Connect Plugin to leverage the Curity Identity Server as a third-party Identity Provider.
Curity Setup
The Kong Dev Portal needs a client configured in the Curity Identity Server. The configuration details below should be sufficient:
- Authentication method:
secret. Make note of the Secret and use it in theclient_secretfield in the Developer Portal configuration (see below). - Capabilities:
Code Flow. - Following scopes:
openid,profile, andemail. - Choose suitable authentication methods.
- Add redirect URI (by default
http://kong-dev-portal:8004/<WORKSPACE_NAME>/auth). - Add the value from
logout_redirect_uriin the below Kong Dev Portal configuration to the list ofAllowed Post Logout Redirect URIsfor the client.
More information is available in the Code Flow tutorial.
Configure OpenID Connect in the Kong Developer Portal
Enabling the Kong Developer Portal is outlined in the Kong Documentation and not covered in this article. The documentation also covers how to configure the OpenID Connect Plugin.
Example Configuration Object
{"redirect_uri": ["https://kong-dev-portal:8004/default/auth"],"consumer_by": ["username","custom_id","id"],"leeway": 1000,"scopes": ["openid","profile","email"],"logout_query_arg": "logout","login_redirect_uri": ["https://kong-dev-portal:8003"],"login_action": "redirect","logout_redirect_uri": ["https://kong-dev-portal:8003"],"ssl_verify": false,"client_id": ["kong-dev-portal-client"],"forbidden_redirect_uri": ["https://kong-dev-portal:8003/unauthorized"],"client_secret": ["Pa$$w0rd!"],"issuer": "https://idsvr.example.com/oauth/v2/oauth-anonymous/","logout_methods": ["GET"],"consumer_claim": ["email"],"login_redirect_mode": "query"}
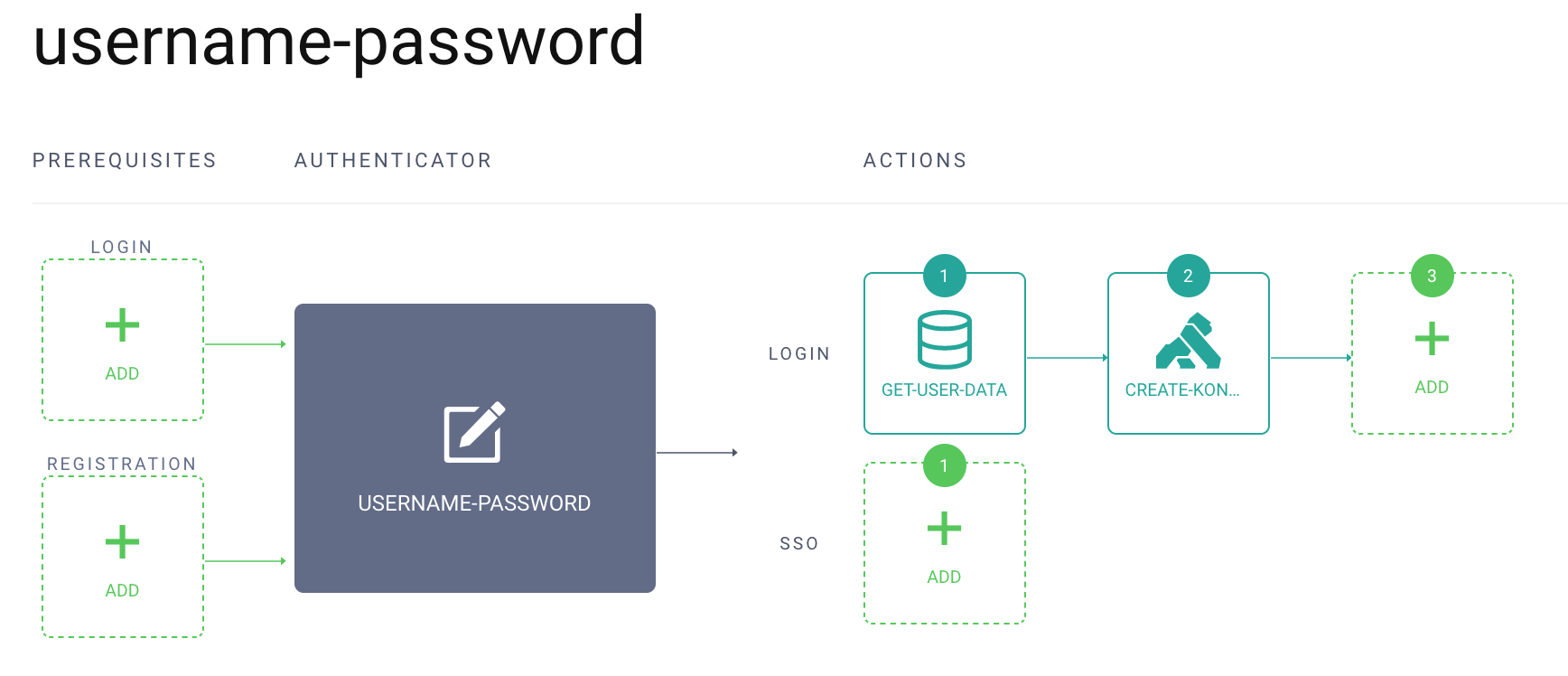
Curity Authentication Action
An Authentication Action to automatically provision the user to the Kong Developer Portal is available in the Curity GitHub repository. Using the Action is not mandatory as the user could be provisioned in other ways, such as manually through the Kong Developer portal login screen. However, using the Authentication Action would streamline the user flow as the Action will take the user's full name and the email from the Curity Authenticator and automatically provision that to the Kong Developer Portal using the exposed API.
The The Kong Developer Portal User Provisioner action is available as open-source and can be forked to fit the needs of the environment as needed.
Configuration
This Action is straightforward to configure. An HTTP Client is needed to communicate with the Kong Dev Portal API. By default, the HTTP Authentication can be left out. Only a correct scheme needs to be configured (HTTP or HTTPS).
The Action also configures the URL to the registration endpoint of the Kong Developer Portal. Here the scheme needs to match what's configured in the HTTP Client used.
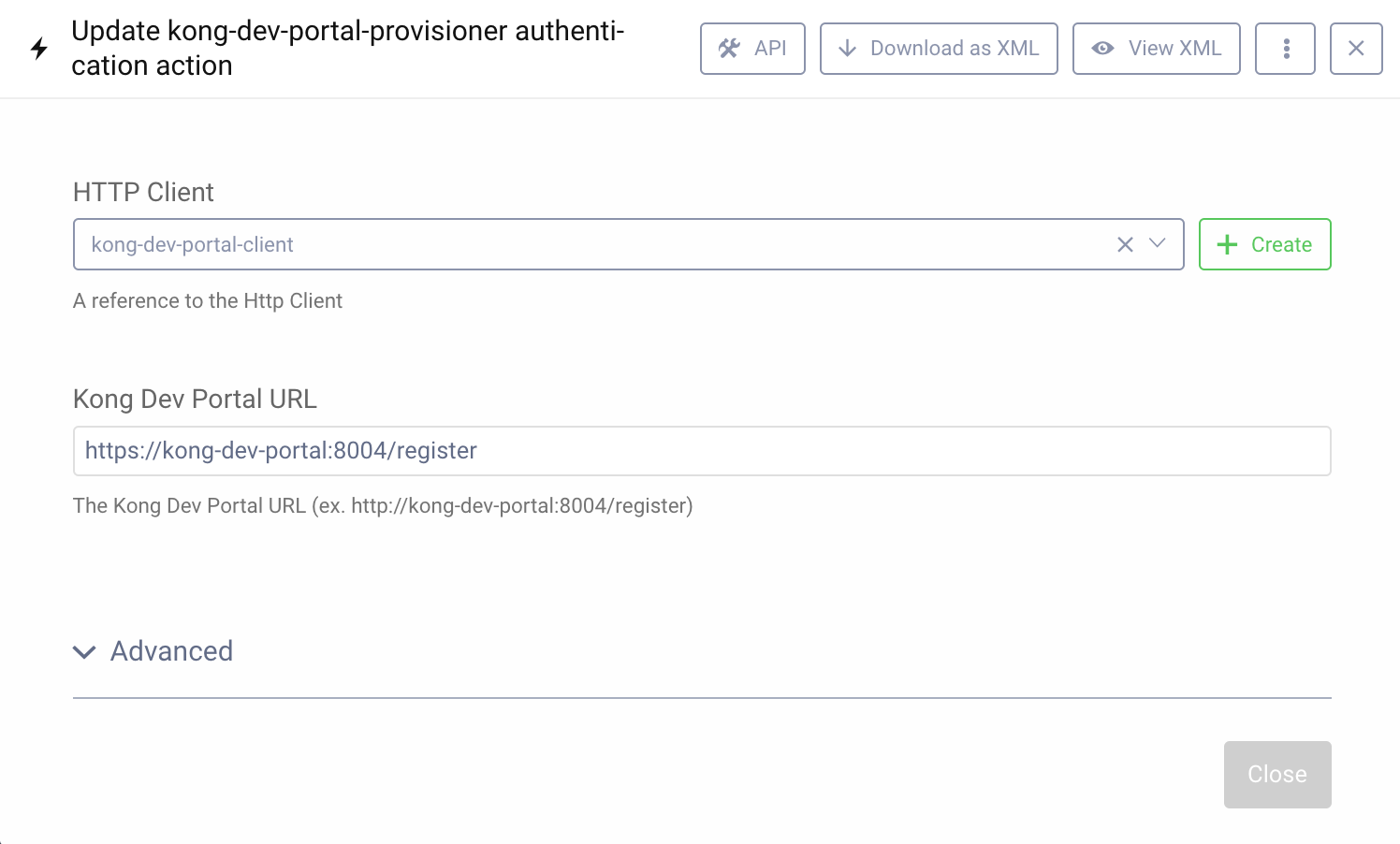
When the action is created, it can be assigned to the Authenticator(s) used in the client configured in the Curity Identity Server as described above.
Action to Resolve Additional User Information
Depending on the Authenticator used, an additional Action may be needed to resolve additional information. By default, The Kong Developer portal provisioning requires Full Name and email. If the Authenticator does not provide this, it's possible to use an Action to resolve the data. This could be as simple as a Data Source action configured to use a Data Source that provides the information.
By default, the Kong Developer Portal Provisioner Action works on the default account table schema of the Curity Identity Server database. This provides email as a column, but the Full Name is not readily available. The Action will operate on the attributes column and parse the information to pass the user's Full name to the Kong Dev Portal.
The attributes column will contain this structure:
{"emails": [{"value": "alice@example.com","primary": true}],"phoneNumbers": [{"value": "555-123-1234","primary": true}],"name": {"givenName": "alice","familyName": "anderson"},"agreeToTerms": "on","urn:se:curity:scim:2.0:Devices": []}
The data source used to resolve additional information needs to be configured with an appropriate Attribute Query. This would look similar to this:
select "email", "attributes" from "accounts" where "username"= :subject
Conclusion
With relatively simple configurations in both the Curity Identity Server and the Kong Developer Portal, it's possible to leverage Curity as the Identity Provider for the Kong Portal. This will provide a very seamless flow for user authentication to the Kong Dev Portal. With the added capability of an Authentication Action, it is possible to automatically provision the user to the Kong Dev Portal for an even more streamlined experience.

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free TrialWas this helpful?



