
Configuring Curity Identity Server as an Identity Provider in Cloudflare
On this page
Cloudflare is a company that provides content delivery network services and its products operate in a reverse proxy architecture in front of websites. The provided services sits between a website's visitor and the hosting provider of the targeted service. As part of its offering, Cloudflare provides an Authentication service called Access, that can leverage external Identity Providers (IDP's) to control access to protected applications and services.
This article serves as a guide on how to configure a Cloudflare Access environment to use the Curity Identity Server as its IDP using the Generic OpenID configuration option that is available to Cloudflare Enterprise customers.
Curity Setup
Create a client or use an existing one. Follow these instructions to configure a client that enables the Code Flow.
Important configurations
openid and email scopes are provided by the client.Configuring Cloudflare Access
Configuring the Login Method
In Cloudflare for Teams, click Access -> Authentication -> Add in the Login methods section and select OpenID Connect
| Parameter Name | Example value |
|---|---|
| Name | Curity |
| Client ID | www |
| Client Secret | Secr3t! |
| Auth URL | The Default URL for a host with the name idsvr.example.com would be https://idsvr.example.com/oauth/v2/oauth-authorize |
| Token URL | The Default URL for a host with the name idsvr.example.com would be https://idsvr.example.com/oauth/v2/oauth-token |
| Certificate URL | The Default URL for a host with the name idsvr.example.com would be https://idsvr.example.com/oauth/v2/jwks |
Callback URL
The Callback URL will depend on the configuration in Cloudflare. The Auth Domain will determine what the complete Callback URL is. If the Auth Domain is example.cloudflareaccess.com the Callback URL will be https://example.cloudflareaccess.com/cdn-cgi/access/callback
Test the configuration
When the configuration has been saved, click Test. A new tab should open in the browser showing the authentication configured for the client configured above. Provided that everything is correctly configured and a successful authentication is performed a confirmation message is displayed
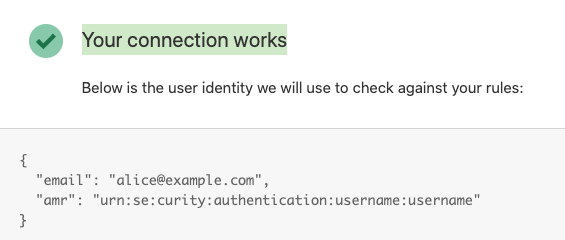
The Login Method should now be saved and available to use throughout the Cloudflare Access configuration.
Configure Access App Launch
One example of where the Login Method can be used is accessing the App Launch page. To configure that and use the newly created Login Method using the Curity Identity Server:
- Go to Access -> Authentication -> App launcher
- Click Set up Access App Launcher
- Add appropriate rules to your environment, Ex. Emails Ending in:
@example.com, then Save - Go to the App Launch page, i.e.
https://example.cloudflareaccess.com/ - A login page should be presented, click Login
- The created Login Method above (Curity) should be available as an option. Click Curity
- This redirects to the Curity Identity Server for authentication using the Authentication method configured in the Client used and gives access to the App Launch page

Note
The user might not have access to any Applications even though Authentication works.
Conclusion
Cloudflare Access with an Enterprise account has out-of-the-box capabilities to leverage an external IDP. With a few simple configuration steps, it is possible to make full use of the capabilities that the Curity Identity Server has to offer for authentication and authorization. The Curity Identity Server can enhance the authentication to Cloudflare protected Applications by:
- Providing many more mechanisms for authentication. For example Duo, WebAuthn, SMS, different Government eID's, social and more authenticators
- Allowing for Multi-Factor and Conditional Multi-Factor Authentication scenarios
- Applying advanced post-authentication workflows without user interactions
Resources
- Configure a client in Curity. Outlined in this article about the Code Flow
- Cloudflare Access
- Cloudflare documentation on Setting up Generic ODIC in Cloudflare

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free TrialWas this helpful?



