On this page
The OpenID AuthZEN Working Group is standardizing fine-grained authorization and simplifying integration. Vendors have previously implemented their own protocols for client-to-server communication and especially the format of the request and response. The AuthZEN protocol standardizes this across all vendors that support the AuthZEN standard. This means that the same client or Policy Enforcement Point (PEP) can send requests to several different Policy Decision Points (PDP) and interpret the response from the PDP. The PEP is vendor agnostic.
Configuration
The configuration is trivial and requires only a few parameters.
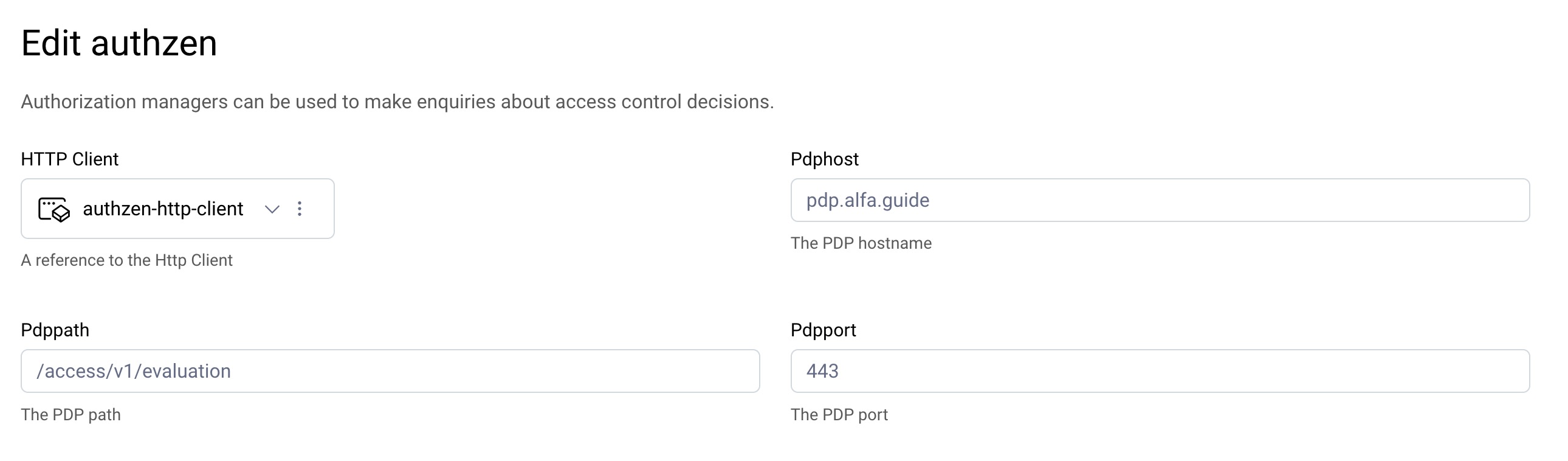
| Config | Description |
|---|---|
| HttpClient | The configuration of the HttpClient to use will differ depending on the PDP that the AuthZEN Authorization Manager communicates with. |
| PDP Host | The hostname of the PDP that supports the AuthZEN standard. |
| PDP Path | This should be the same for all AuthZEN enabled PDP and can most likely be left as the default /access/v1/evaluation |
| PDP Port | The port the PDP is exposed on. |
The Request
The authorization request sent to the PDP is constructed by the plugin.
{"subject": {"type": "user","id": "alice"},"resource": {"type": "api","id": "user-management"},"action": {"name": "can_read","properties": {"method": "POST"}}}
The id of the user (alice in the above example) is the subject of the token in the request that is invoking the authorization manager.
The resource type is always api. The id is set to the API type that the current request calls. In the example above the user management GraphQL API is called.
The Response
In the current version of AuthZEN (1.0) there is only a boolean answer for the authorization decision. This makes the response very simple, its either true or false. In the future, AuthZEN plans to augment this with for example obligations. This would require an update to this implementation but would allow for data filtration of the response.
{"decision":false}
Summary
There are many ways to handle fine-grained authorization. The Curity Identity Server ships with several Authorization Managers out-of-the-box and there are more available as plugins on GitHub.
The AuthZEN Authorization Manager implements the protocol defined by the OpenID AuthZEN Working Group. By implementing the protocol, the authorization manager supports several authorization servers/vendors without the need for vendor specific implementations.
Resources

Join our Newsletter
Get the latest on identity management, API Security and authentication straight to your inbox.

Start Free Trial
Try the Curity Identity Server for Free. Get up and running in 10 minutes.
Start Free TrialWas this helpful?






